How Zero Trust Security Promises to Cast a Wide Net On Spear-Phishers
Zero trust security is a fundamental security concept that introduces additional scrutiny around access to systems and data, not only from external [...]
DETAIL
How to Meet NIST SP-800-171v2 Access Control Practices for Remote Data Access
How to Use Zero Trust to Meet NIST SP-800-171v2 Access Control Practices for Remote Data Access The Zero Trust Data Access architecture [...]
DETAIL
Using Zero Trust Architecture (ZTA) to Protect Remote Data Access
Using Zero Trust Architecture (ZTA) to Protect Remote Data Access WHAT ABOUT THE DATA? Zero Trust Architecture (ZTA) is fast becoming the […]
How to Meet CMMC Access Control Practices for Remote Data Access
How to Use Zero Trust to Meet CMMC Access Control Practices for Remote Data Access The Zero Trust Data Access architecture of [...]
DETAIL
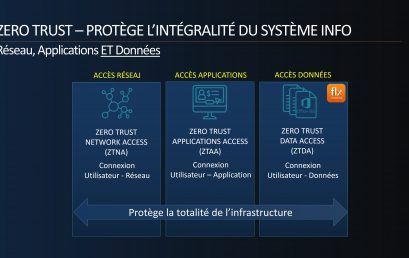
Pourquoi Zero Trust. Pourquoi maintenant?
Le principe du Zero Trust (confiance zéro) est très simple : ne faites jamais confiance et vérifiez toujours chaque transaction. Cela protège [...]
DETAIL
Making the Case for ZTDA Has Never Been More Obvious
Making the Case for ZTDA Has Never Been More Obvious ZTDA or Zero Trust Data Access technology is needed now more than […]
How to Meet NIST Guidelines for Zero Trust for Remote Data Access
The National Institute of Standards and Technology (NIST) has produced NIST Special Publication 800-207 outlining Zero Trust principles and guidelines that can [...]
DETAIL
Why Zero Trust and Why Now?
The principle behind zero trust is very simple - never trust and always verify every transaction. This protects your organization in ways [...]
DETAIL
Comment protéger vos données avec Zero Trust Data Access (ZTDA)
Comment protéger vos données avec Zero Trust Data Access (ZTDA) Temps de lecture estimé: 6 minutes Avec l’augmentation du télétravail, [...]
DETAIL
How to Protect Your Data with Zero Trust Data Access (ZTDA)
Implementing a Zero Trust Network Access platform and/or a Zero Trust Application Access platform is a good start, but ultimately is not [...]
DETAIL